Awdl - Awdl 24



Abstractly, physmaps are virtual mappings of all of physical memory The physmap is typically a 1:1 virtual mapping of physical memory.


Description: Keep all your products and IoT devices up to date to stay safe.
Sexy:
Funny:
Views: 870
Date: 19.02.2022
Favorited: 172

Category: DEFAULT
User Comments 3

Plenty of vulnerabilities which a skilled vulnerability researcher would consider low-hanging fruit can require reaching a program point that no fuzzer today will be able to reach, no matter the compute resources used.
More Photos
Latest Photos
Latest Comments
- +428reps
- From a troubleshooting point of view, with a bunch of clients only occasionally fritzing the network to share a file of a business card, maybe nobody notices.
- By: Robison
- +352reps
- Larger groups could even have people dedicated to building custom reversing tools.
- By: Greenberg
- +131reps
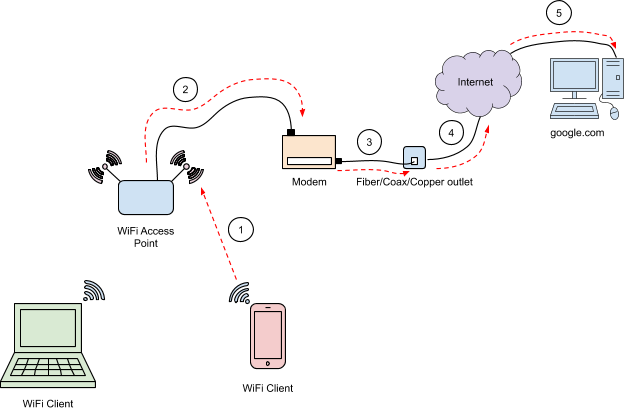
- Most people's experience with WiFi involves connecting to an infrastructure network.
- By: Jase
- +604reps
- Vulnerability discovery remains a fairly linear function of time invested.
- By: Annecorinne
- +54reps
- The attacks allow crashing Apple devices in proximity by injecting specially crafted frames.
- By: Pistol
pussy.pages.dev - 2022
DISCLAIMER: All models on pussy.pages.dev adult site are 18 years or older. pussy.pages.dev has a zero-tolerance policy against ILLEGAL pornography. All galleries and links are provided by 3rd parties. We have no control over the content of these pages. We take no responsibility for the content on any website which we link to, please use your own discretion while surfing the porn links.
Contact us | Privacy Policy | 18 USC 2257 | DMCA
DISCLAIMER: All models on pussy.pages.dev adult site are 18 years or older. pussy.pages.dev has a zero-tolerance policy against ILLEGAL pornography. All galleries and links are provided by 3rd parties. We have no control over the content of these pages. We take no responsibility for the content on any website which we link to, please use your own discretion while surfing the porn links.
Contact us | Privacy Policy | 18 USC 2257 | DMCA


































